Eximius Hardware Key
Problem Statement
According to statista.com, in 2019, the number of data breaches in the United States amounted to 1,473 with over 164.68 million sensitive records exposed. Of the data breaches studied in the 2019 Cost of a Data Breach Report, 24% of which are caused by human errors, and the average cost of one is $8.19 million in the United States. Human errors consist of actions such as the use of malware infected devices, falling prey to phishing attacks and social engineering.
Multi-Factor Authentication (MFA) better secures user accounts than traditional passwords, hence preventing data breaches caused by certain human errors. However, there still exist vulnerabilities in the current state-of-the-art hardware keys. In the event of loss or theft, a YubiKey remains trusted on the owner's account, which gives malicious actors an opportunity to compromise the account by gaining access to the YubiKey. Even the soon-to-come YubiKey Bio is subject to such attack, since fingerprint lifting is a well-known technique. We then present the Eximius Hardware Key that closes this gap and takes the state-of-the-art hardware security keys to the next level.
Solution
The Eximius Hardware Key introduces the following security features to your everyday Internet user:
Malware Detection
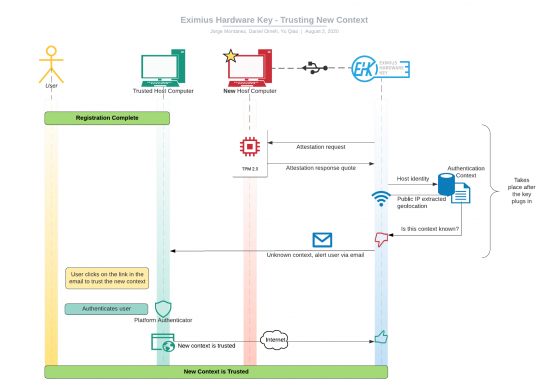
- The system leverages Trusted Platform Modules (TPMs) to measure the state of connected devices ensuring they are in a trustworthy state.
- Upon detection of untrusted and/or malicious software the system will prevent the user from authenticating.
Contextual Multi-Factor Authentication (CMFA)
We recognize that PINs are subject to social engineering attacks, so they shouldn't be the only factor that authorizes a user to the hardware key, and any subsequent accounts that the user is trying to access with the key (i.e. online banking).
- The system learns what a valid authentication context is based on the user's security requirements.
- Unexpected contexts will require email confirmation and authorization from a previously trusted host device.
Theft Resistant
The Eximius Hardware Key will not be usable under an untrusted authentication context. If it is lost or stolen, all conditions of an existing trusted context must be met for the key to be used.
User Defined Security
Security Requirements can be customized to meet user requirements. For instance,
- User can selectively trust new authentication contexts.
- User can disable contextual authentication, falling back to using just the PIN.
Special Thanks
Special thanks go to the following individuals and organization for supporting us through this project.
- Center for Long-Term Cybersecurity (CLTC) for funding
- Prof. Matthew Garrett for providing great insights on Trusted Platform Modules (TPMs)
- Prof. Sajad Khorsandroo for providing great insights on network signatures
- Prof. Ryan Liu and Prof. Sekhar Sarukkai for supporting us throughout this entire journey
Course
Social Engineering Figure Credit: sapannpix - Fotolia
Video
If you require video captions for accessibility and this video does not have captions, click here to request video captioning.