That’s a Hard Pass
Problem Statement
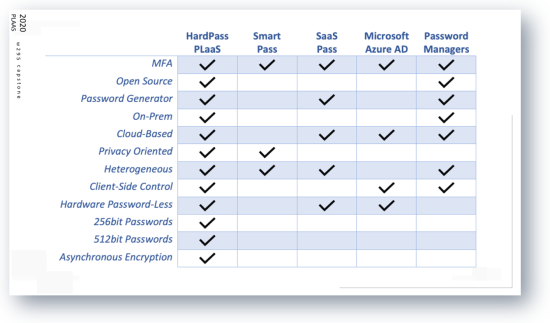
Passwords have been the main method of authentication for a long time, but they have also become a massive weak point. Hackers now engage in credential harvesting as an access vector, and the latest Verizon security report reveals that weak, default, or stolen passwords were involved in 81% of data breaches. While Multi-Factor authentication has been added to mitigate these weaknesses, it has introduced new challenges such as additional implementation complexity, reduced ease of use, and lack of adoption on web applications. In the market today, there are many solutions that attempt to resolve the issues with passwords, but our forward-thinking approach, Password-Less as a Service (PLaaS), provides an in-cloud password manager that encrypts all data client side before it is cloud stored using a simple hardware token.
Solution
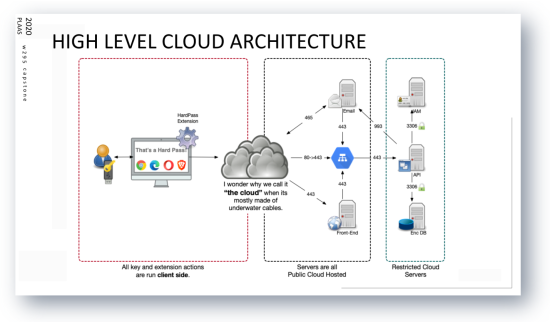
We are redefining authentication with an emerging technology. Our approach is convenient and secure by combining a simple pin with a hardware key for passwordless authentication (similar to how a debit card or military CAC card is set up). Users can login to our website from any location using the hardware key and pin. They will also be able to store all their passwords securely online. Additionally, we developed a JavaScript Extension that pulls credentials from the cloud, decrypts them client side and submits them to webforms on behalf of the user. The backend was developed using Python packages with infrastructure hosted on Azure cloud.
Our deliverable is a Hardware-based YubiKey to access websites using a physical tap and pin. We are using FIDO2 (WebAUTHN for CTAP2) to allow users to sign-up and login without a password to web based forms. Registration to our service leads to generating an asynchronous keypair that is transparent to the user. From there, we use the Yubikey and onboard public key for encryption of the data locally. The data is only transmitted after encryption. Lastly, we used the previously established private key on the Yubikey for decryption of the data locally. All key and extension actions are run client side. As such, data will be encrypted client side and transmitted as is, so there is no risk of data disclosure if our backend infrastructure is breached.
Our method is different from other hardware key based authentication because it is compatible with any browser that supports full FIDO2 and we do not manage any sensitive data. Our approach will set up Password-Less as a Service (PLaaS) and our main stakeholders will be Executives and Security Professionals who understand the risks with existing solutions. We created a usable design so that end users will have a seamless experience with simple prompts for action which will make adoption easy for everyone including technophobes and inexperienced users.