Open Bounty
Problem Statement
The lack of transparent and data-driven pricing mechanisms in bug bounty programs poses significant challenges for companies that offer bug bounties and researchers who submit vulnerabilities. Companies risk setting incorrect incentives for their bug bounty programs, leading to a false sense of security for not being able to attract competent talent, or missing out on the disclosure of vulnerabilities altogether, and leaving the door open to malicious actors exploiting the discovered vulnerabilities instead. Bug hunters, on the other hand, often get bullied into accepting a lower reward during the triage process, where companies downplay the significance of discovered vulnerabilities and pressure them to accept lower payouts. To address these issues, there is a need for a transparent and accurate evidence-backed oracle that estimates the price of security vulnerabilities, ensuring adequate compensation to incentivize bug hunters to properly disclose vulnerabilities and provide a benchmark for companies to price bug bounties.
Solution
A data-driven price recommendation engine for security vulnerabilities.
Significance and Benefit
Our capstone project, OpenBounty, is designed to tackle a primary issue in the current cybersecurity field: the absence of a transparent and objective pricing mechanism in bug bounty programs. This shortfall has resulted in false security for companies and the risk of driving bounty hunters towards exploiting vulnerabilities rather than disclosing them responsibly.
Our goal is to create a more balanced and equitable bug bounty ecosystem. To this end, we're introducing an innovative machine learning tool. By using a blend of historical payout data, geographical location, and company profiles, our tool provides data-driven, evidence-backed pricing estimates. This promotes a climate of transparency and healthy competition in the bug bounty field.
By ensuring fair and adequate compensation, our tool indirectly encourages more secure cyber practices. It incentivizes bounty hunters to disclose vulnerabilities rather than exploit them and helps companies compete on prices by attracting the appropriate level of talent. This allows companies to gauge whether they've effectively addressed their vulnerabilities or if their bounty offerings are insufficient to attract skilled bug hunters.
By introducing a user-friendly platform, we're aiming to standardize the bug bounty price markets. Powered by machine learning, our solution brings fairness and transparency to bug bounty compensation, advancing us towards our goal of a balanced and equitable bug bounty ecosystem.
We aim to enhance the behaviors of the two-sided bug bounty market, promoting fairness and preventing companies from pressuring bug hunters into accepting undervalued compensation.
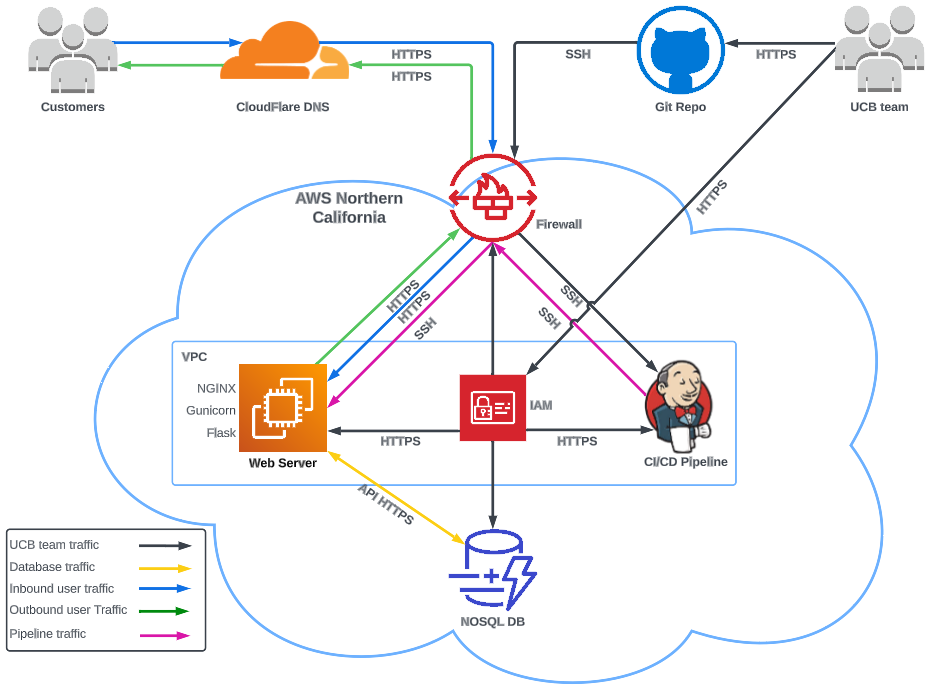
Security Architecture
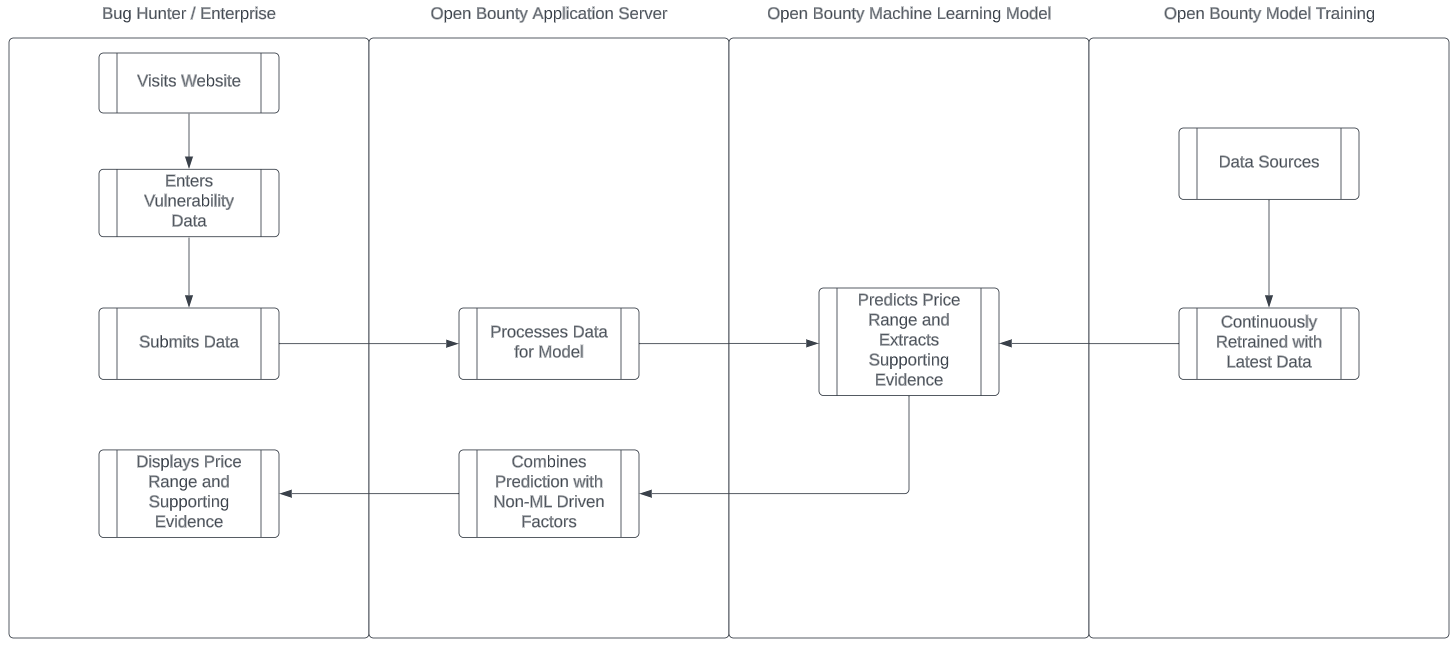
Sequence Diagram
Try it yourself!
Try out OpenBounty to generate evidence based price estimates www.OpenBounty.com
Acknowledgements
The OpenBounty team is thankful for the guidance, support, and invaluable insights of their advisors Clarence Chio (UC Berkeley Lecturer) and Dr. Jennia Hizver (UC Berkeley Lecturer).
The team would also like to thank Ryan Liu and Dr. Sekhar Sarukai for their guidance throughout the the development of OpenBounty.
And finally, a thank you to Pascal Issa (UC Berkeley Lecturer), BugCrowd, Oak Security, and fellow Security Researchers for their valuable input and support.