PatrIoT Security
Problem Statement
Internet of Things (IoT) devices have surged in popularity over the last few years due to their unprecedented ability to bridge the physical and digital worlds and simplify the lives of those who use them at extremely low price points. However, more often than not these products are designed insecurely resulting in their compromise by malicious actors. In fact, more than half of the Distributed Denial of Service (DDoS) attacks seen by Netscout in the first half of 2021 were a result of IoT botnets.
Compromised IoT devices can pose extreme risks to everyone in cyberspace - for example being on the receiving end of a distributed attack, loss of productivity resulting from inoperable devices, or the reputational risk of having an attack originate from one’s own network. Thus, it is critical to be able to detect when a device has been compromised and react before further damage occurs.
Project Description
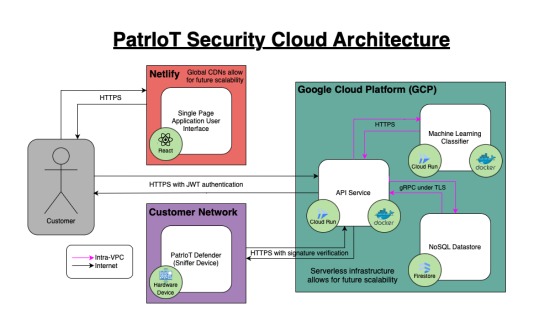
Security should be ubiquitous and transparent, not complex, costly or burdensome. This is the core principle that we at PatrIoT Security believe in and let guide us in what we do. We have developed a machine learning based IoT threat detection solution which focuses on the user with simplicity and privacy in mind.
Passwordless Authentication
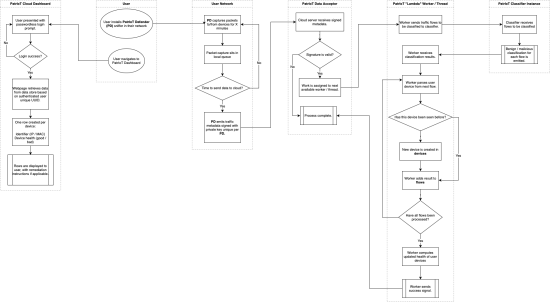
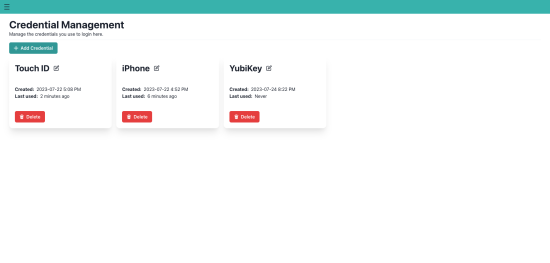
Our commitment to a simple user experience starts with how users authenticate to access their device dashboard. We opted to do away with passwords entirely and have embraced the modern WebAuthn passwordless authentication standard.
Traditionally, users would be responsible for picking a unique password for every account they created, and if they reused passwords across accounts then any resulting compromise was solely their responsibility. By utilizing WebAuthn, we have shifted the burden off the user at no cost to security or privacy. The registration and authentication process is now greatly simplified, and by default enforces multi-factor authentication without requiring any extra steps on the user’s part.
From a technical security perspective, this also makes the backend database a much less attractive target for attackers. Where traditional authentication models would require storing hashed passwords - which could subsequently be cracked and reused on other websites, we only store authenticator public keys which are of no use to attackers.
User Interface
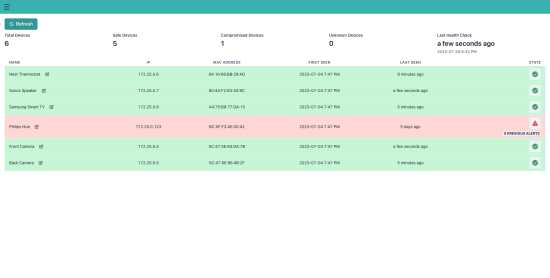
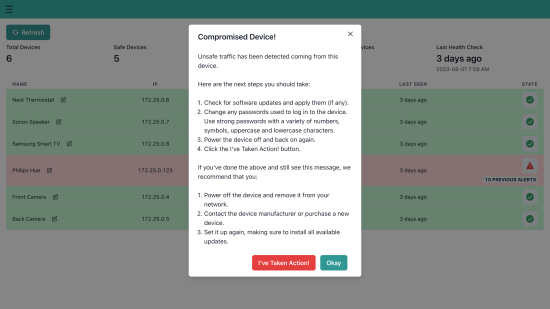
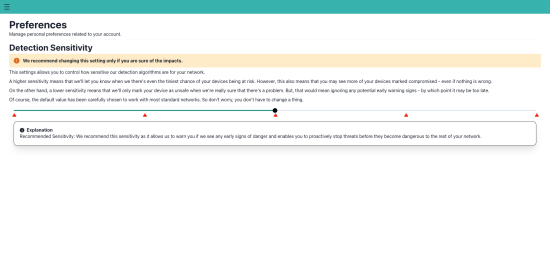
Our user interface itself - and particularly the device dashboard showing users the health of their devices - was designed with simplicity at its core. Rather than provide our users with complex documentation detailing how to use our product, we have designed the interface to clearly and concisely guide the user in plain language. There are no complex statistics or values that would cause a user to wonder what they mean - just a straightforward indicator of the health of their device. And should one of their devices be detected as compromised, we present helpful advice and instructions to guide them through the remediation process.
Machine Learning
The machine learning backed analysis of network traffic to identify malicious traffic is a core component of our product. However, even though this process is entirely transparent to the user, we still developed it keeping the user in mind. The core focus was to maintain user data privacy without compromising on identification accuracy. As a result, our algorithm does not rely on the actual data being transmitted within the network packets. Instead, we utilize various pieces of metadata - or information about the traffic itself - in order to identify potential malicious activity.
Acknowledgements
The PatrIoT Security team would like to acknowledge the following individuals for their guidance and advice throughout the project:
- Clarence Chio
- Richard Cziva
- Ryan Liu
- Dr. Sekhar Sarukkai
We would also like to cite the following datasets used in the development of our machine learning model:
- The Aposemat IoT-23 dataset:
- Sebastian Garcia, Agustin Parmisano, & Maria Jose Erquiaga. (2020). IoT-23: A labeled dataset with malicious and benign IoT network traffic (Version 1.0.0) [Data set]. Zenodo. http://doi.org/10.5281/zenodo.4743746
- The University of New South Wales TON_IoT datasets
- Moustafa, Nour. "A new distributed architecture for evaluating AI-based security systems at the edge: Network TON_IoT datasets." Sustainable Cities and Society (2021): 102994. Public Access Here.
- Booij, Tim M., Irina Chiscop, Erik Meeuwissen, Nour Moustafa, and Frank TH den Hartog. "ToN IoT-The role of heterogeneity and the need for standardization of features and attack types in IoT network intrusion datasets." IEEE Internet of Things Journal (2021). Public Access Here.
- Alsaedi, Abdullah, Nour Moustafa, Zahir Tari, Abdun Mahmood, and Adnan Anwar. "TON_IoT telemetry dataset: a new generation dataset of IoT and IIoT for data-driven Intrusion Detection Systems." IEEE Access 8 (2020): 165130-165150.
- Moustafa, Nour, M. Keshk, E. Debie and H. Janicke, "Federated TON_IoT Windows Datasets for Evaluating AI-Based Security Applications," 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), 2020, pp. 848-855, doi: 10.1109/TrustCom50675.2020.00114. Public Access Here.
- Moustafa, Nour, M. Ahmed and S. Ahmed, "Data Analytics-Enabled Intrusion Detection: Evaluations of ToN_IoT Linux Datasets," 2020 IEEE 19th International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom), 2020, pp. 727-735, doi: 10.1109/TrustCom50675.2020.00100. Public Access Here.
- Moustafa, Nour. "New Generations of Internet of Things Datasets for Cybersecurity Applications based Machine Learning: TON_IoT Datasets." Proceedings of the eResearch Australasia Conference, Brisbane, Australia. 2019.
- Moustafa, Nour. "A systemic IoT-Fog-Cloud architecture for big-data analytics and cyber security systems: a review of fog computing." arXiv preprint arXiv:1906.01055 (2019).
- Ashraf, Javed, Marwa Keshk, Nour Moustafa, Mohamed Abdel-Basset, Hasnat Khurshid, Asim D. Bakhshi, and Reham R. Mostafa. "IoTBoT-IDS: A Novel Statistical Learning-enabled Botnet Detection Framework for Protecting Networks of Smart Cities." Sustainable Cities and Society (2021): 103041.