SecuriKey
Problem Statement
Small businesses and non-profit organizations encounter significant challenges in addressing cybersecurity risks due to a lack of resources, expertise, and affordable solutions. These entities often find themselves ill-equipped to safeguard their assets and data. To mitigate the risks of cyber threats, it's essential to continuously manage software assets and maintain vigilance in identifying vulnerabilities. However, due to the lack of necessary expertise, knowledge, and cost-effective tools, these organizations remain exposed to potential security breaches.
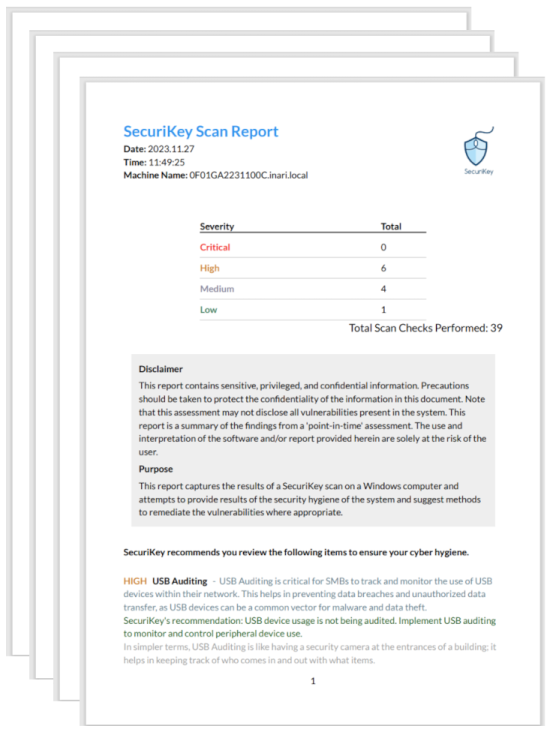
Alarming statistics reveal that there were 789 Common Vulnerabilities and Exposures (CVEs) linked to security misconfigurations. Notably, Microsoft's Office Suite, which is commonly used for daily work activities, ranked among the top assets affected by breaches and was a frequent target of system intrusion attacks. SecuriKey can be deployed to scan these potentially compromised systems for vulnerabilities and threats, efficiently closing the existing security gap.
SecuriKey: Your Trusted Solution
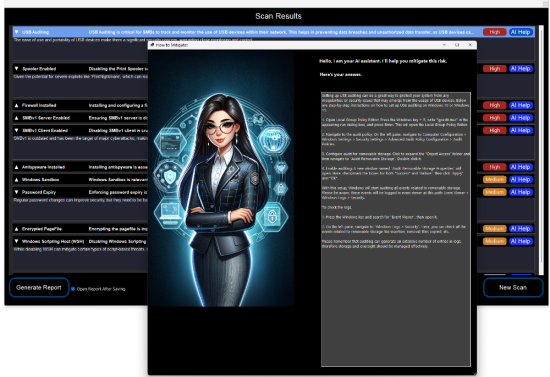
SecuriKey is a user-friendly, portable application that rapidly evaluates host PC security and recommends actionable solutions for vulnerabilities. As your trusted cybersecurity partner, SecuriKey empowers small businesses and non-profit organizations, as well as individuals to swiftly assess their system's security posture. It provides transparent recommendations for bolstering defenses and mitigating vulnerabilities. The process is seamless - just plug in SecuriKey to your computer, and you'll effortlessly receive personalized security guidance, ensuring a seamless path to enhancing your digital safety.
FAQs
- Q> Is SecuriKey scanning invasive?
- A> SecuriKey simplifies the process of securing Windows-based machines by analyzing your computer's settings for common misconfigurations and insecure defaults. SecuriKey only provides recommendations on improving your cybersecurity hygiene. SecuriKey never makes changes to your computer.
- Q> What types of analyses and insights does SecuriKey offer?
- A>
- System Security Assessments
- Customized Scans for Industry-Specific Regulations
- Generate encrypted reports to collaborate seamlessly with trusted security experts and enhance your cyber defense strategy
- AI assistant guides users in layman's terms, providing step-by-step instructions for implementing remediations.
- Q> Is SecuriKey hard to set up and maintain?
- A> The setup and maintenance of SecuriKey are straightforward. The application operates seamlessly as a standalone executable, requiring no installation. For detailed instructions, please refer to the comprehensive SecuriKey User Guide available at the provided link below.
Future Enhancements
Development
- Introduce additional scanning capabilities for a more comprehensive cybersecurity assessment.
- Extend compatibility to additional operating systems beyond Windows.
Testing
- Conduct real-world testing with small businesses to validate and tailor features to their specific needs.
Community Engagement
- Foster Adoption: Actively engage with small businesses and nonprofits to encourage the adoption of SecuriKey.
- Collect Feedback: Establish robust mechanisms for ongoing user feedback to refine and enhance SecuriKey continually.
- Open Source Contributions: Invite contributions from the cybersecurity community to strengthen SecuriKey's capabilities through collaboration.
Acknowledgement
The SecuriKey team would like to express its sincere appreciation for the invaluable guidance and feedback provided by Capstone Instructor Ryan Liu and Dr. Sekhar Sarukkai. Additionally, the team extends its heartfelt gratitude to the MICS Faculty and fellow MICS Students for their support and collaboration.